Deterministic Controls for Production AI Agents

Keep agents from going rogue with monitoring, access controls, and automated least privilege.
Permissions for LLMs and Agents
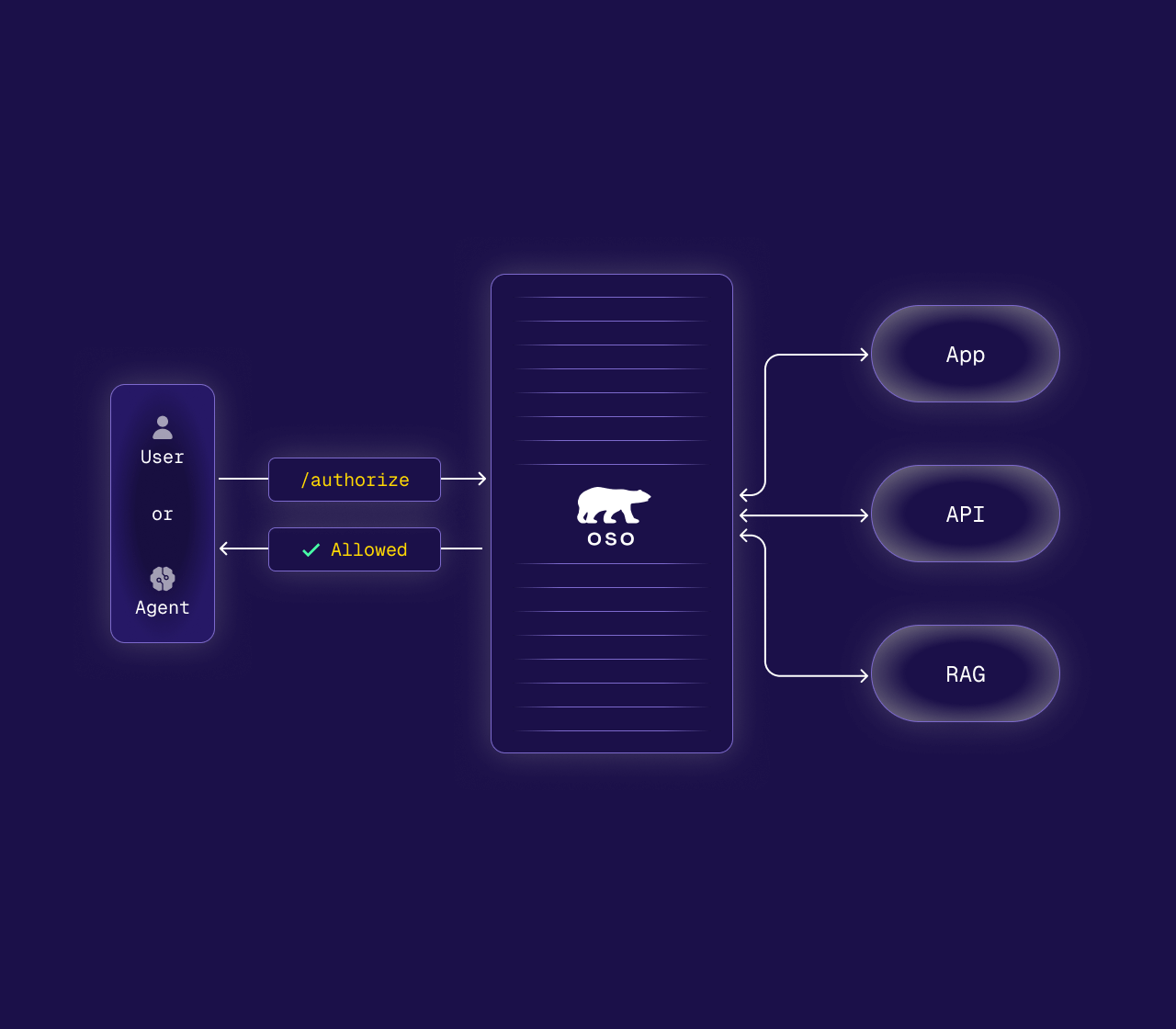
LLM Authorization
Define permissions in one place and enforce them for human and LLM users alike
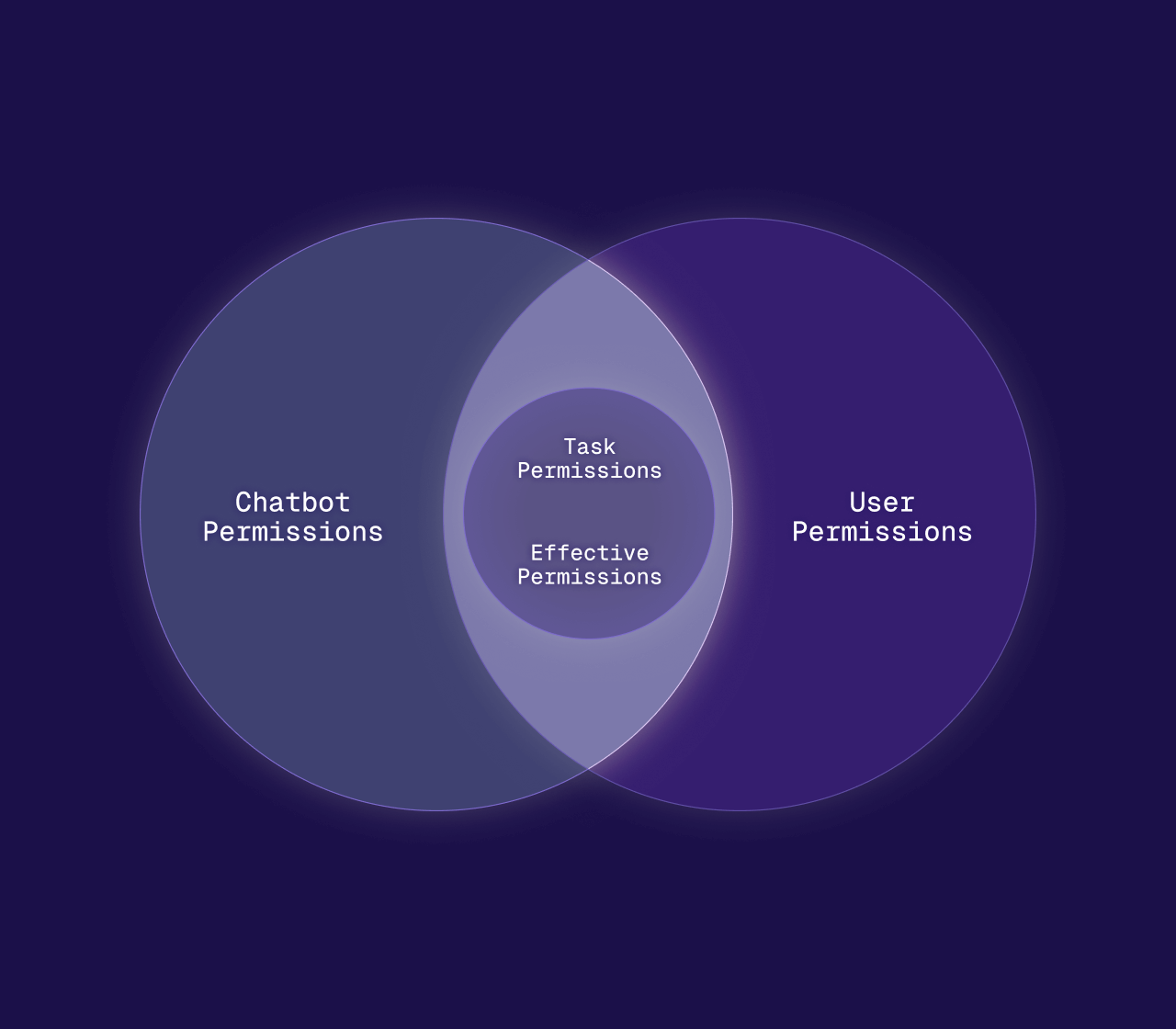
RAG Apps
Build Retrieval-Augmented Generation that adds context without leaking data

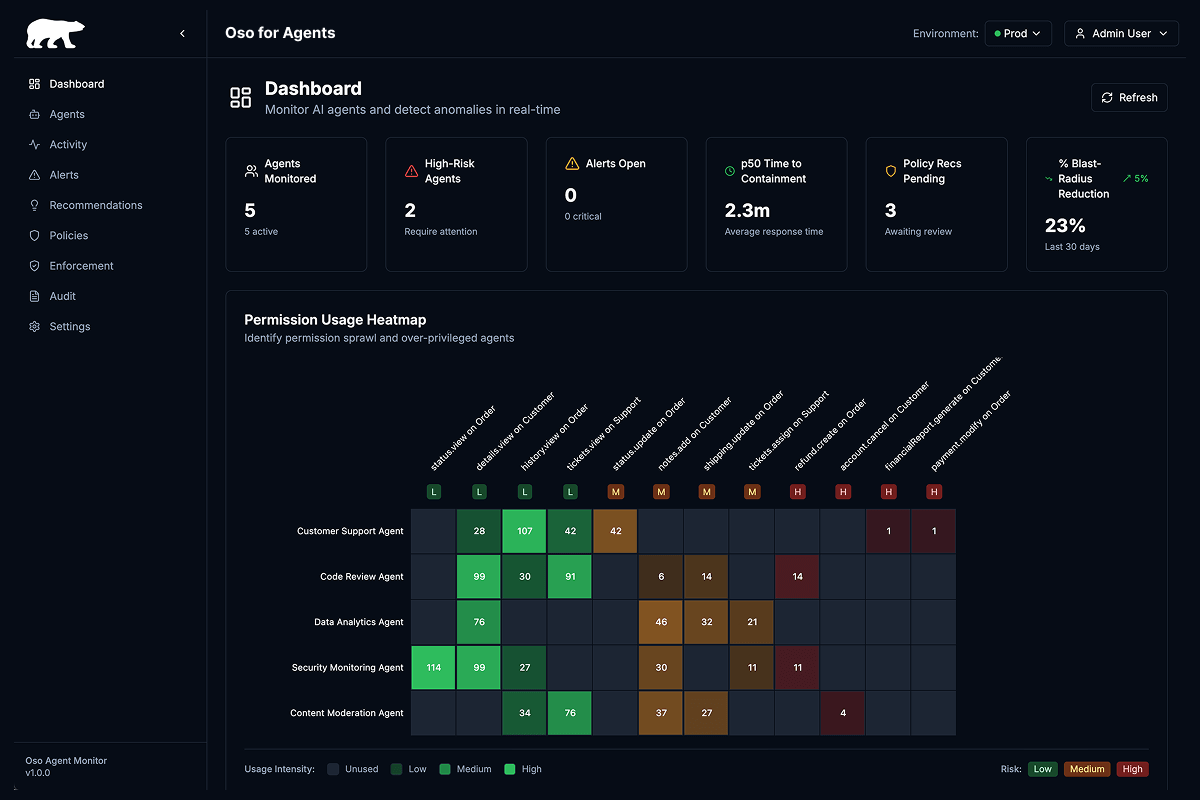
Agents
Monitor agents’ actions and scope permissions down to least privilege
Built for the critical path

Case Studies
Adopted Oso as a centralized authorization platform, enabling faster delivery of secure, agentic AI applications.
Unified RBAC, ReBAC, and ABAC into a single, maintainable framework using Oso’s declarative policy language—enabling reusable, consistent access logic across services—while Oso Cloud delivered fast, compliant authorization checks close to local HR data.
Replaced the legacy system with Oso Cloud and built dashboards and APIs on top of Polar, enabling business self-service and eliminating manual code changes.
Brex cuts thousands of lines of auth code, achieves sub-10 ms P99 performance, and gains 4× engineering efficiency with Oso’s centralized authorization.
Centralized complex permission logic without syncing sensitive data, simplifying development and debugging.
Delivered centralized, versioned policies that streamlined complex access control across services, with enterprise-grade audit logs and dashboards enabling transparent reporting to meet stringent compliance requirements.
Eliminated infrastructure overhead, standardized global access, and enabled fine-grained RBAC and ABAC via Polar—giving engineers the tools to model real-world access while ensuring low-latency, resilient authorization with geo-replicated environments.
Developer Love
A Single Permissions Layer for Applications, RAG, and Agents
Define your policy once, plug in your data, and enforce authorization consistently across your systems.



























