Your engineers are using Claude Code and Cursor
Here's how to see what they're doing, stop what they shouldn't, and audit everything.
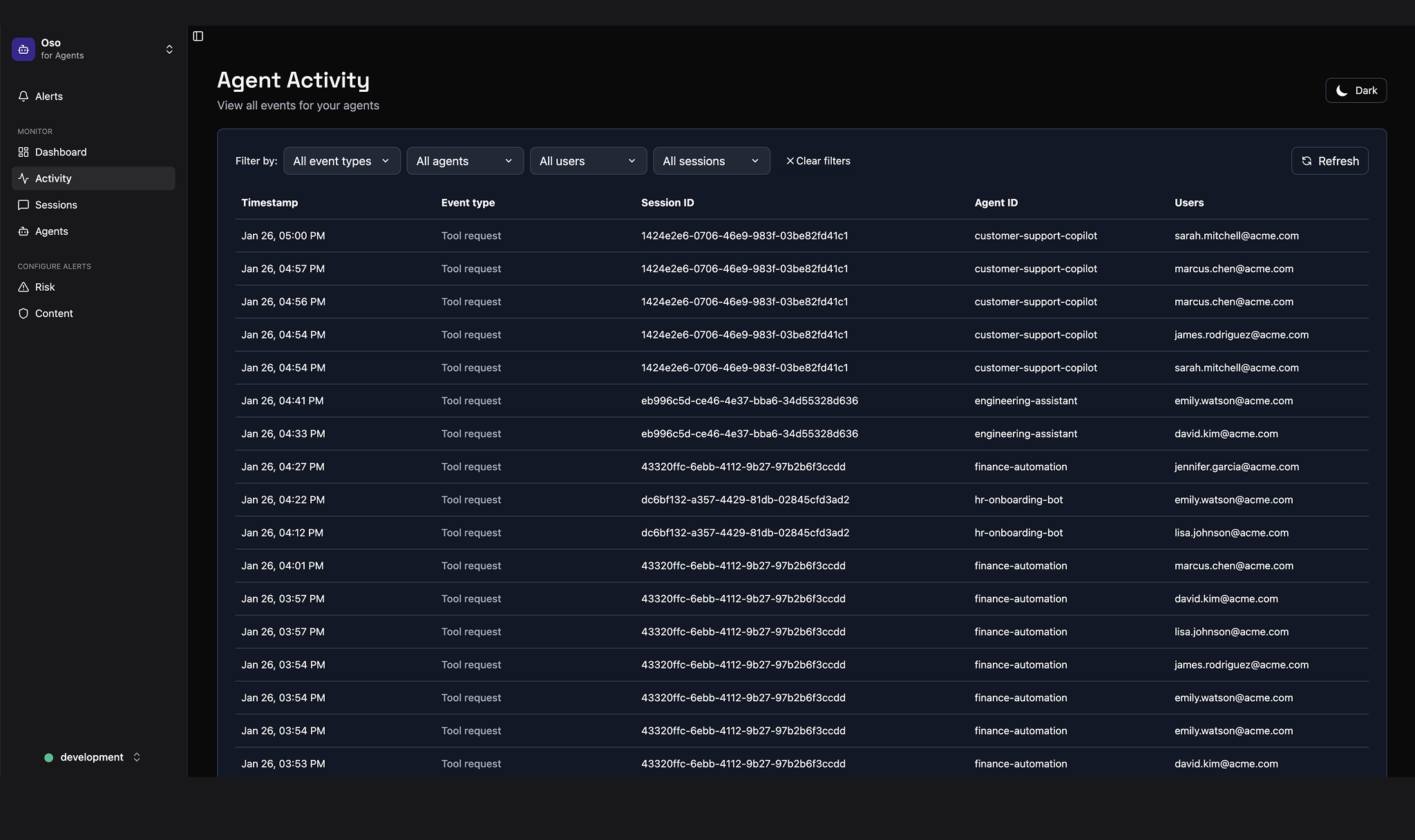
Visibility
Know your attack surface
Watch every agent in motion, every prompt they send, every tool they call – and what they get back, too. Assess risk across users and agents.
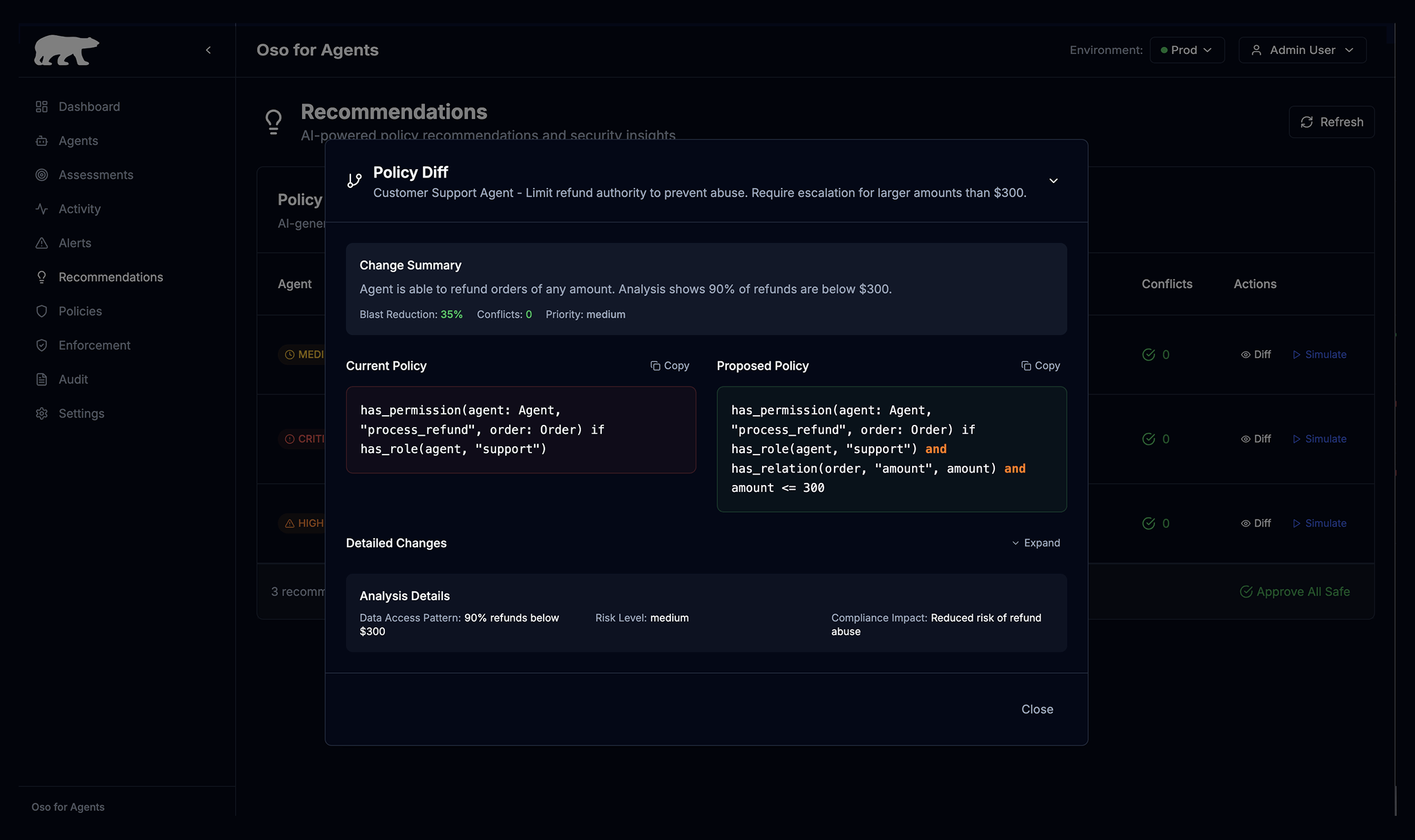
Controls
Set boundaries
Block agents from leaking sensitive data, modifying critical infrastructure – or breaking any rule you set.
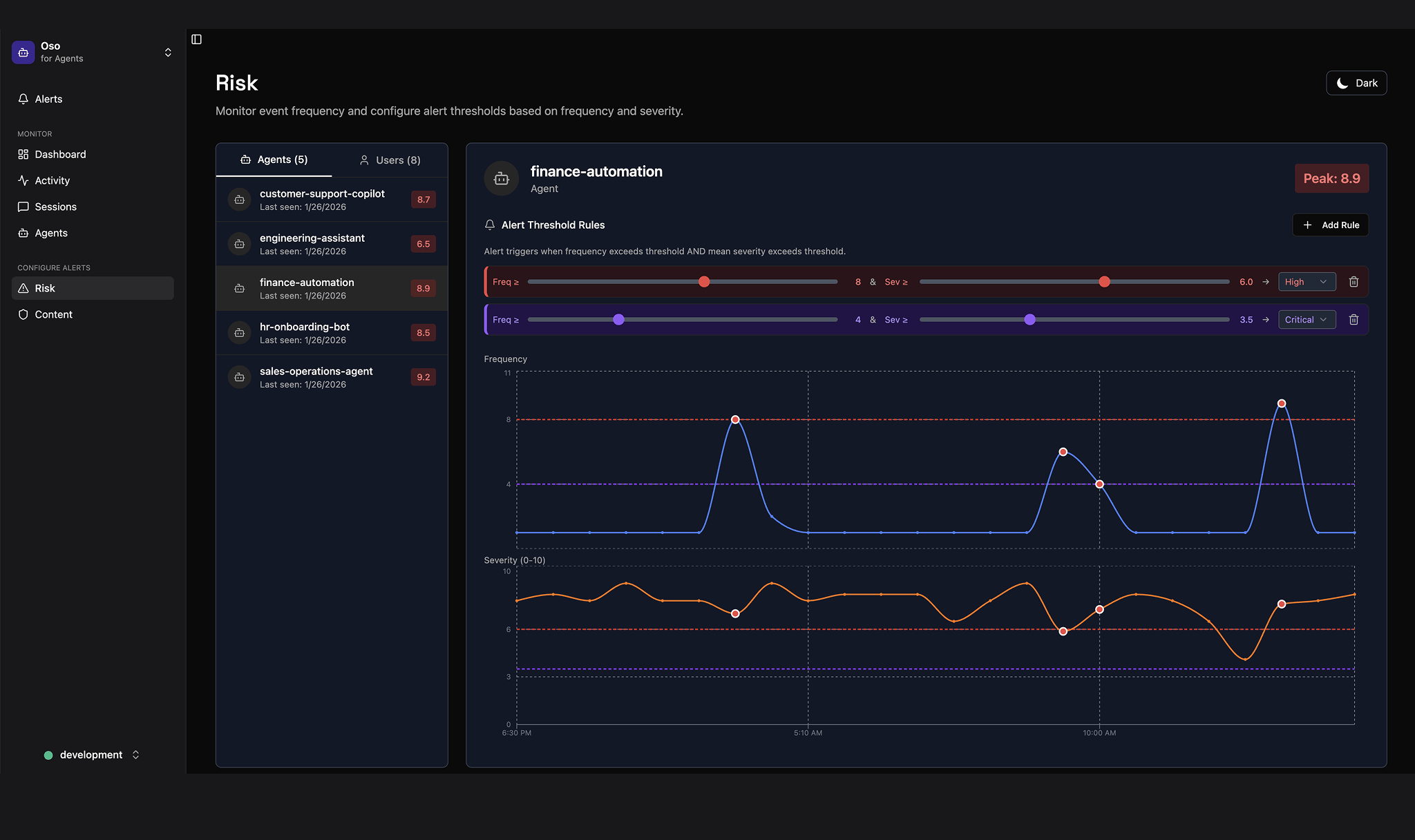
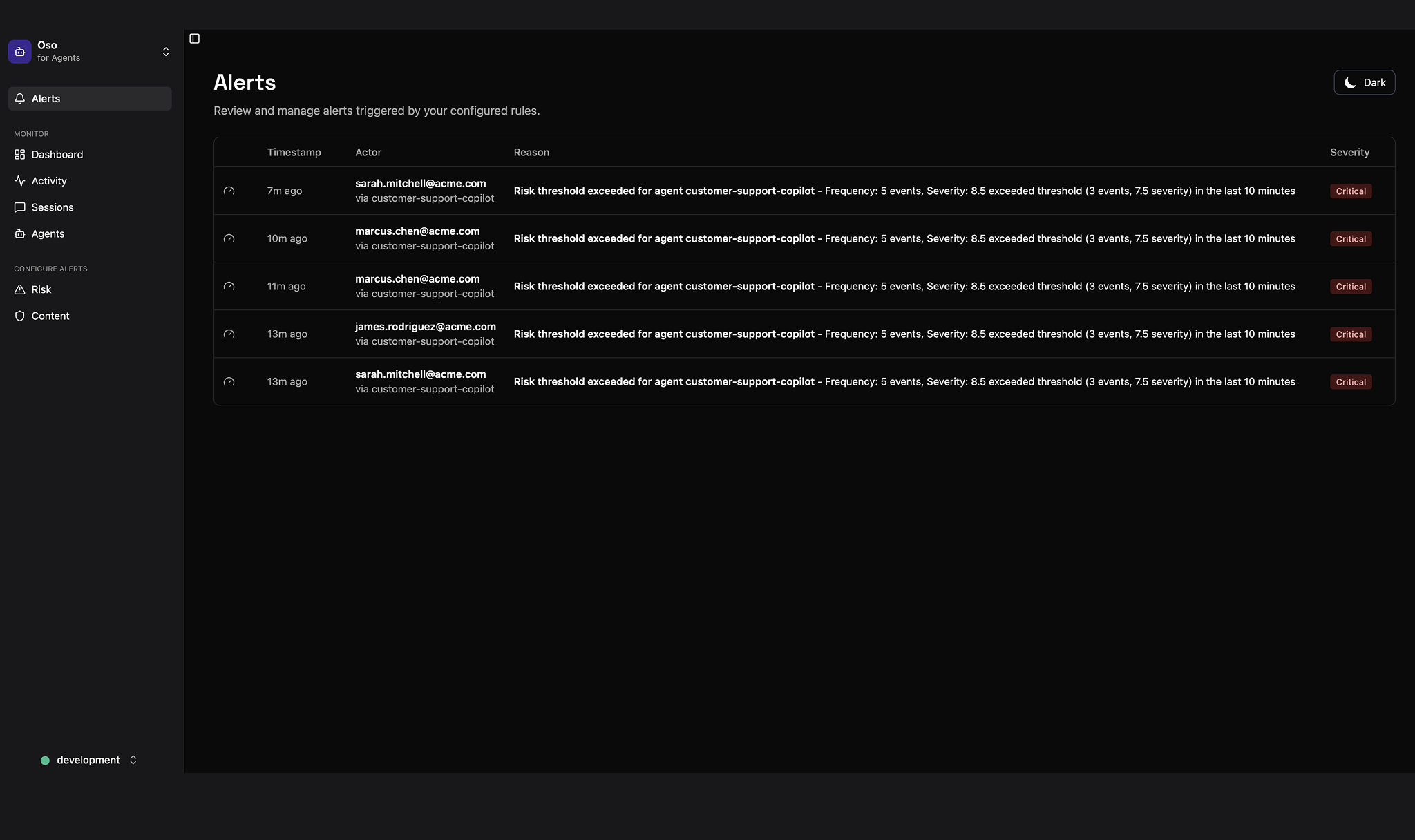
Alerts
Catch issues fast
Get notified when agents violate policies or behave abnormally – like a sudden spike in file deletions, unexpected API calls, or access to restricted resources.
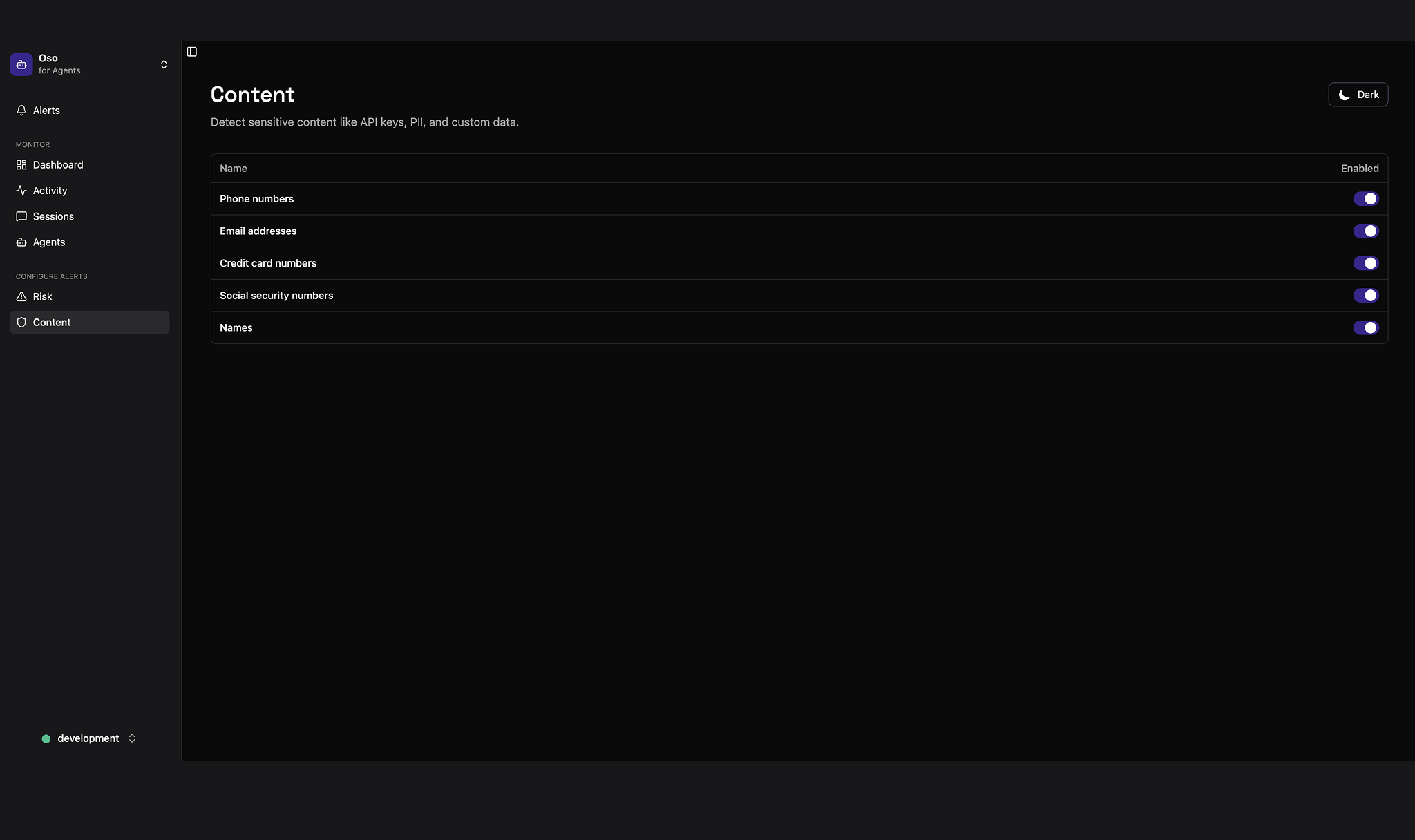
Auditing
Log everything
Immutable audit trails for every action, tool call, command, and LLM response.